Quantum computing is rapidly emerging as a transformative technology that has the potential to revolutionize industries and fields such as cryptography, medicine, artificial intelligence, and more. One area where the influence of quantum computing is particularly profound is cybersecurity. While quantum computers promise incredible computing power, they also pose serious threats to current encryption standards and data security methods. This article explores how advancements in quantum computing impact cybersecurity, the challenges posed by quantum technologies, and how the cybersecurity landscape can adapt to this new reality.
Understanding Quantum Computing and Its Potential
What is Quantum Computing?
Quantum computing is a type of computation that leverages the principles of quantum mechanics, the branch of physics that deals with the behavior of matter and light on the atomic and subatomic scale. Unlike classical computers that use bits to process information as either 0 or 1, quantum computers use quantum bits (qubits), which can exist in multiple states at once due to the phenomenon known as superposition. This allows quantum computers to perform complex calculations at speeds that are unattainable for classical systems.
The Promise of Quantum Computing
Quantum computing has the potential to revolutionize industries by solving problems that are too complex for classical computers. Fields like drug discovery, material science, and artificial intelligence stand to benefit significantly from quantum advancements. However, with great power comes great responsibility, especially when it comes to data security.
The Quantum Threat to Cybersecurity
Breaking Modern Encryption Protocols
Public-Key Cryptography: A Prime Target
One of the most significant threats quantum computing poses to cybersecurity is its ability to break widely used encryption methods, particularly public-key cryptography. Public-key cryptography relies on mathematical problems, such as the factoring of large prime numbers, which are difficult and time-consuming for classical computers to solve.
For example, RSA encryption, one of the most widely used encryption algorithms today, relies on the difficulty of factoring large numbers into their prime components. While classical computers would require an infeasible amount of time to break RSA encryption, a sufficiently powerful quantum computer using Shor’s algorithm could break it in a matter of hours or even minutes.
- RSA and ECC Vulnerabilities: Both RSA and elliptic-curve cryptography (ECC), which rely on complex mathematical problems, are highly vulnerable to quantum attacks. Once quantum computers reach a certain level of capability, they will be able to crack these encryption methods, rendering them obsolete for securing data.
Symmetric Encryption and Quantum Computers
Unlike public-key cryptography, symmetric encryption algorithms like AES (Advanced Encryption Standard) are generally more resistant to quantum attacks. However, quantum computers can still use Grover’s algorithm, which provides a quadratic speedup for brute-force attacks. While AES encryption can still be used with larger key sizes (e.g., AES-256), quantum computers still pose a potential threat if they continue to advance.
The Impact on Data Privacy and Confidentiality
Data Harvesting for Future Decryption
A significant concern in the cybersecurity space is the concept of “store now, decrypt later” attacks. Malicious actors could collect encrypted data today with the intention of decrypting it once quantum computers become sufficiently powerful. Sensitive information such as financial data, government secrets, or personal communications could be at risk if it falls into the wrong hands.
- Future-Proofing Data: Organizations must consider how to protect sensitive data in the present while also preparing for the future quantum threat. This means investing in quantum-resistant encryption technologies that can stand the test of time.
Threats to Blockchain and Cryptocurrencies
Blockchain technology and cryptocurrencies, such as Bitcoin and Ethereum, are also vulnerable to quantum computing advancements. Blockchain relies on cryptographic algorithms like ECC to secure transactions and verify identities. Once quantum computers can break ECC, they could potentially reverse blockchain transactions or take control of cryptocurrency wallets, leading to a loss of trust in the decentralized financial ecosystem.
Quantum-Resistant Cryptography: The Solution?
The Emergence of Post-Quantum Cryptography
As the quantum threat to cybersecurity becomes more apparent, researchers and cryptographers have been working on developing quantum-resistant or post-quantum cryptography (PQC). These new cryptographic algorithms are designed to withstand attacks from quantum computers while maintaining security on classical machines.
- Lattice-Based Cryptography: One of the leading candidates for post-quantum cryptography is lattice-based cryptography, which relies on mathematical problems that are difficult for both classical and quantum computers to solve.
- Hash-Based Cryptography: Hash-based cryptography uses cryptographic hash functions to secure data and has shown promising results in resisting quantum attacks.
- Multivariate Polynomial Cryptography: This approach involves solving multivariate quadratic equations, which quantum computers find challenging to compute efficiently.
The Role of Standardization
As post-quantum cryptographic algorithms are being developed, international organizations such as the National Institute of Standards and Technology (NIST) are working on standardizing quantum-resistant encryption methods. These standards will guide governments, businesses, and industries on how to transition from current encryption practices to quantum-safe methods.
- NIST Post-Quantum Cryptography Competition: NIST has been running a global competition to evaluate and standardize new cryptographic algorithms that are resilient to quantum computing attacks. The finalists are expected to be announced soon, paving the way for widespread adoption of quantum-resistant encryption.
The Future of Cybersecurity in a Quantum World
Enhancing Security Protocols
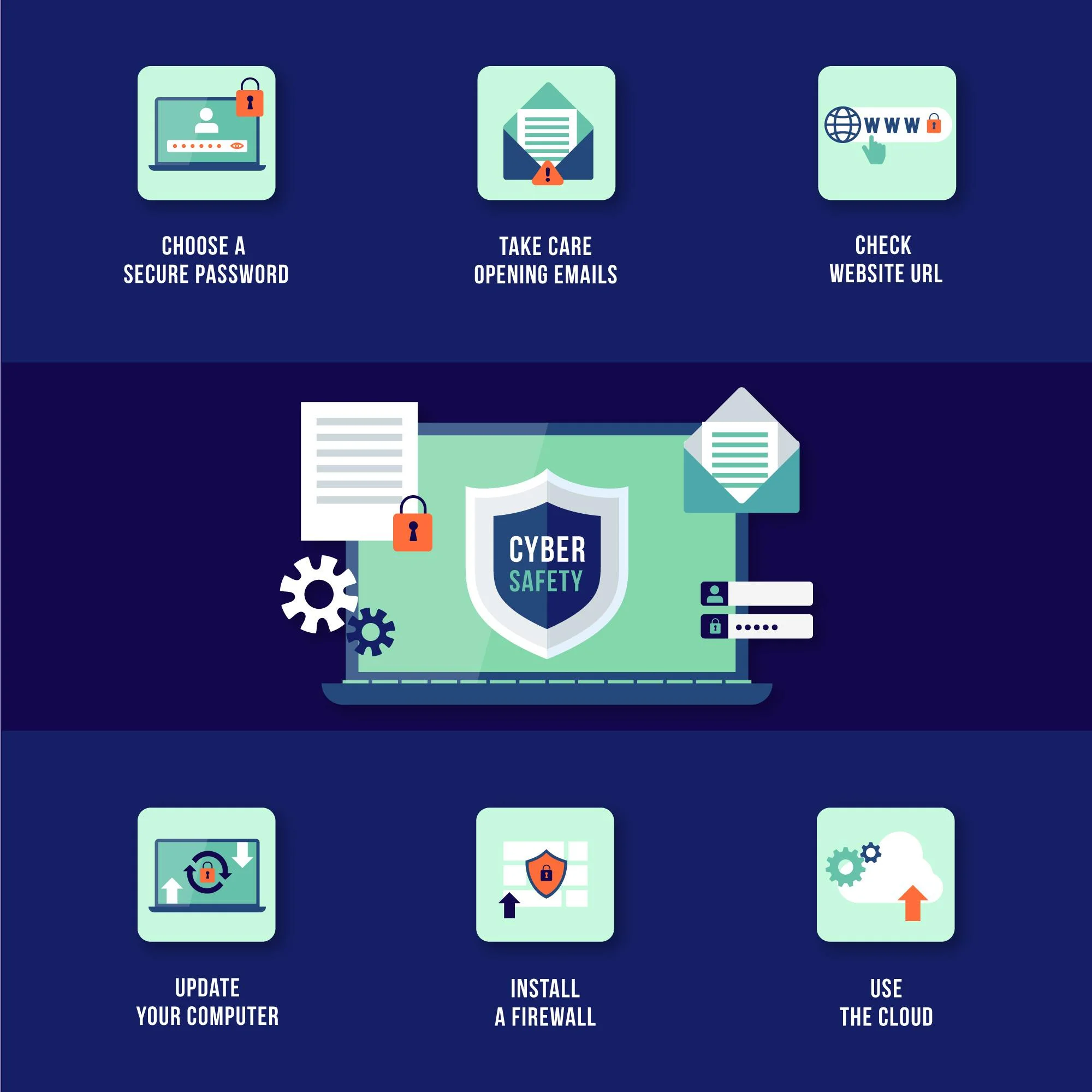
As we approach the era of quantum computing, cybersecurity will need to evolve significantly. Organizations should take proactive steps to adopt quantum-safe encryption methods, update their security protocols, and train their workforce on the risks associated with quantum technologies.
- Key Management Systems: Quantum computing will also require a rethinking of key management systems. Ensuring that cryptographic keys are securely generated, stored, and rotated will be critical in a quantum-resistant security infrastructure.
- Hybrid Cryptographic Systems: Some experts suggest using a hybrid approach, where quantum-resistant algorithms are used alongside classical cryptographic methods to ensure additional layers of protection as quantum computing continues to evolve.
Quantum Key Distribution (QKD): A New Frontier
Another promising solution to the quantum cybersecurity challenge is quantum key distribution (QKD). QKD uses the principles of quantum mechanics to secure the transmission of cryptographic keys. The unique feature of QKD is that any attempt to intercept or eavesdrop on the key exchange would disturb the quantum state, alerting the parties involved.
- Benefits of QKD: By leveraging the principles of quantum physics, QKD ensures that cryptographic keys remain secure even in the presence of quantum computers. It is being tested in several industries as a way to enhance data security in the quantum era.
- Challenges of QKD: While QKD offers promising security, it is still in its early stages of development and requires significant infrastructure investments, such as specialized fiber optic networks.
Quantum-Safe Architecture
The future of cybersecurity will likely see the development of quantum-safe architectures that integrate multiple layers of security. From post-quantum cryptography to QKD, building a robust and scalable infrastructure that can withstand quantum computing threats will be essential for organizations looking to protect sensitive data.
Conclusion: Preparing for the Quantum Future
The rapid advancements in quantum computing represent a double-edged sword. While the technology promises breakthroughs in numerous fields, it also poses a significant threat to current cybersecurity systems. The ability of quantum computers to break widely used encryption methods, disrupt blockchain technology, and compromise data privacy presents an unprecedented challenge for cybersecurity professionals.
However, the development of quantum-resistant cryptography, post-quantum encryption, and emerging technologies like quantum key distribution offer hope in mitigating these risks. As the world transitions into the quantum era, governments, businesses, and industries must act swiftly to secure their digital infrastructure and prepare for a future where quantum computing becomes mainstream.
In this new digital age, quantum cybersecurity will play a critical role in safeguarding our data, communications, and global financial systems. By staying ahead of the curve and adopting forward-looking security measures, we can embrace the benefits of quantum computing while minimizing its risks to the cybersecurity landscape.